Privacy And Security at iotum
At iotum, we prioritize the security and privacy of our partners’ and users' communications. Explore below to understand how we safeguard your meetings, data, and privacy.

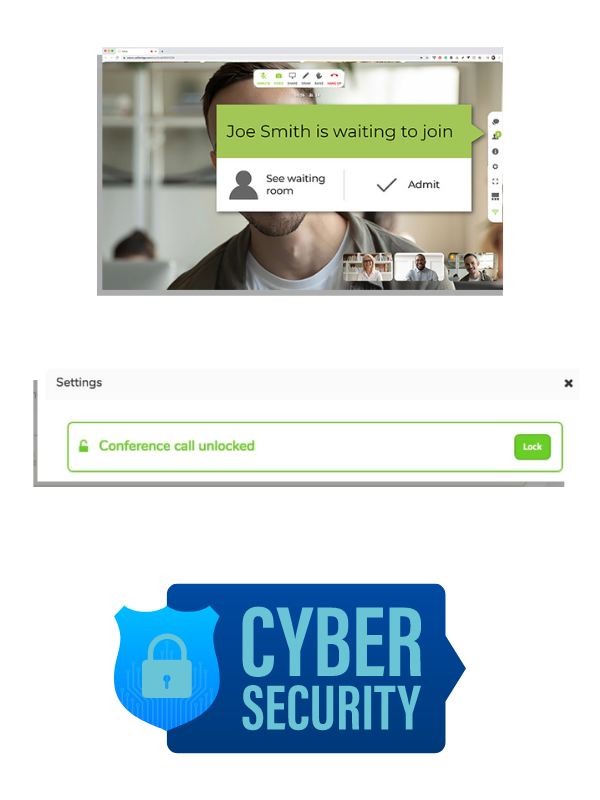
Security Overview
Privacy and security are fundamental values at iotum. We offer a comprehensive suite of tools to safeguard your meetings, empowering hosts to manage their meetings, participant activity and information effectively. Here are some key in-meeting security capabilities available to our users:
- Encrypted meetings are enabled by default, with optional End-to-End Encryption (E2EE).
- Utilize Waiting Rooms to screen attendees before granting access.
- Require the host’s presence before the meeting begins.
- Expel or suspend participants as needed.
- Lock meetings to prevent unauthorized access.
- Enable/disable recording permissions for participants.
- Implement passcodes to secure meetings.
Protecting Your Data
We employ robust encryption protocols to safeguard your data during transmission and storage:
- Communications are established using TLS encryption.
- Meeting, webinar, and messaging content are encrypted using 256-bit Advanced Encryption Standard (AES).
- Optional Audio and Video End-to-End Encryption ensures that only meeting participants have access to cryptographic keys, ensuring maximum privacy.


Recordings are securely stored in our cloud, ensuring the integrity and confidentiality of your data:
- Cloud recordings are encrypted and controlled by account owners.
- Recordings are encrypted at rest using 256-bit Advanced Encryption Standard (AES).
- Recordings and file transfers are encrypted and can be set to be deleted within a set amount of time (set by you).
Protecting Your Privacy

- Various authentication methods, including OAuth, and Password-based, with optional Two-Factor Authentication (2FA).
- Seamless integration with enterprise identity management platforms for streamlined user provisioning.
- Managed domains for automatic user addition and group provisioning.
- Continuous compliance with industry standards and certifications.
iotum’s Certificates and Standards
At iotum, we adhere to the highest standards of compliance to ensure the security and privacy of our users’ data. Our commitment to safeguarding sensitive information is reflected in our compliance with industry-leading regulations and standards:

GDPR Compliance
iotum is fully compliant with the General Data Protection Regulation (GDPR), ensuring that the processing and protection of personal data of individuals within the European Union (EU) are in accordance with GDPR requirements.
CASL Compliance
We adhere to the Canadian Anti-Spam Legislation (CASL), which governs the use of electronic messaging and the installation of computer programs to prevent spam and unauthorized access to computer systems.
HIPAA Compliance
iotum complies with the Health Insurance Portability and Accountability Act (HIPAA), ensuring the confidentiality, integrity, and availability of protected health information (PHI) shared through our platform.
SOC2 Compliance (In Progress)
We are currently in the process of completing our SOC2 compliance, demonstrating our commitment to implementing stringent controls and procedures to secure our systems and protect user data.
Our dedication to regulatory compliance underscores our ongoing efforts to maintain the trust and confidence of our users while upholding the highest standards of security and privacy. For more information about our compliance measures, please contact us.
Security Resources
Explore our Security Resources for comprehensive information on our security practices, certifications, standards, and attestations.